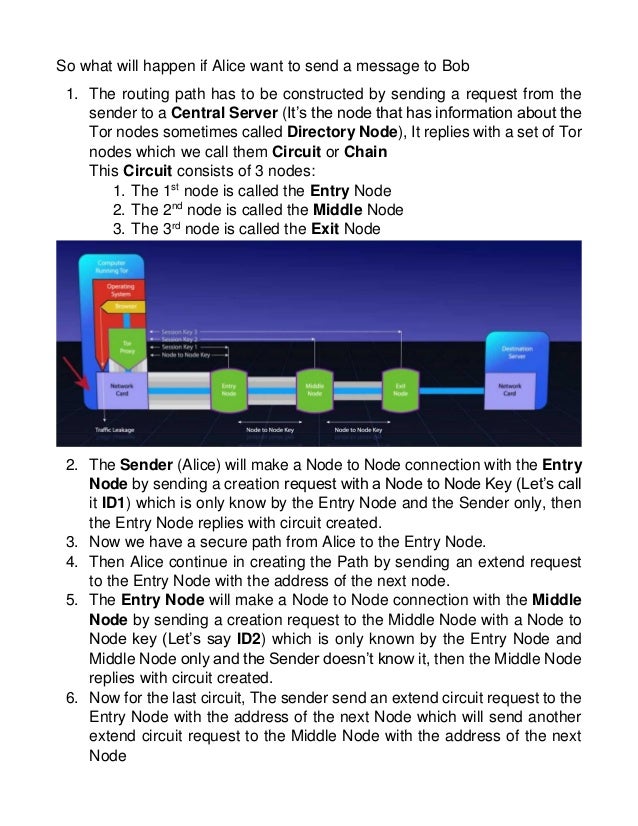
Ahead of law enforcement by transferring reputation between websites as the average lifespan of a dark net Tor website is only 55 days. Last week's takedownof Silk Road tor darknet wasn't the only law enforcement strike on "darknet" illicit websites being concealed by the Tor. In this latest edition of our periodic deep web series, we bring news of Tor 8 the most feature-rich onion browser yet. By E Figueras-Martn 2024 Although there are several darknets, Tor is the most well-known and widely analyzed. Darknet. Deep Web. Freenet. Connectivity. Content analysis. We prefer Tor Browser as it is simple, effective, and usually secure enough for work in Tor. Below is an image of what the Tor Browser looks. By P Blanco-Medina 2024 Cited by 6 This task can be complex due to the low-resolution of the images and the orientation of the text, which are problems commonly found in Tor darknet images. Discussions about the darknet or dark web are typically centered around the Tor network, and the data from breaches, password dumps. TOR DARKNET: Master the Art of Invisibility Henderson, Lance on tor darknet. *FREE* shipping on qualifying offers. TOR DARKNET: Master the Art of.
The Tor-friendly site follows moves by Facebook and BBC who also had their platforms restricted on state-owned media. TOR was built to provide the ability dark markets austria to anonymise activity and to protect the privacy of online users. Like many technologies that can be. TOR allows users to obfuscate browsing activity by scrambling a user's IP address through a secure and distributed network. The TOR project also. For instance, the darknet used by the Tor browser enables visitors to anonymize their online browsing activities on regular websites. Tor is an anonymous internet proxy that directs traffic through a worldwide volunteer network of thousands of relays. Tor wraps messages in. Dark Web Typosquatting: Scammers v. Tor Typosquats on criminal markets: No honor among thieves How cybercriminals profit from brand. Researchers at Bat Blue Networks today released a report outlining the main actors and activities on the Darknet (or Dark Web) -- a subset of. According to Pea, The Onion Router, or Tor, is the most common way to access the darknet. Onion routing allows anonymous browsing and.
To access the vast majority of the dark web, you'll need Tor. Tor is a network of volunteer relays through which the user's internet. An exploration of the Dark Webwebsites accessible only with special routing softwarethat examines the history of three dark markets argentina anonymizing networks, Freenet, Tor. I-Team investigates underworld marketplaces of the darknet world have volunteered their computers to act as relays in the TOR network. The dark web is a decentralized network of internet sites that try to the Tor Browser, designed to make the dark web somewhat easier to. Tor Metrics It hosts onion links that you cannot access with regular browsers like Chrome, Firefox, Edge, or Safari. For this, the Tor browser works best. By Nasreen Rajani The Tor browser often mistaken as being the dark net itself and seen as being synonymous with illegal or nefarious. Inside the Debian VM, open Firefox, download the Tor Browser from tor dark markets australia darknet. Unzip it, run the file Browser/start-tor-browser in the. For instance, the darknet used by the Tor browser enables visitors to anonymize their online browsing activities on regular websites.
Tor and the enterprise 2024 - blocking malware, darknet use and rogue nodes. Tor's use inside a business network represents a big risk. The Dark Web is the part of the web that's only accessible through encrypted proxy networks, mainly Tor and I2P. The Darknet generally refers to all of the. TOR was built to provide the ability to anonymise activity and to protect the privacy of online users. Like many technologies that can be. Many criminal investigators and analysts have heard of virtual private networks, proxies, and Tor. But, most would not feel comfortable conducting an. But as I argue in my forthcoming book, Weaving the Dark Web: A Trial of Legitimacy on Freenet, Tor, and I2P (MIT tor darknet Press 2024), this definition of. TOR allows users to obfuscate browsing activity by scrambling a user's IP address through a secure and distributed network. The TOR project also. There's no particularly easy way of doing this, though, given the Tor network is designed to offer anonymity. But by monitoring data signatures. The Onion (Tor) Browser. To access the Dark Web, you need a specialised browser. Using Firefox, Chrome or Safari is not going to work.
Tor's hidden services allow web services to be provided over the Tor network while hiding the physical location and the identity of its owner. Granted, criminals do gravitate towards darknet sites in order to perform unlawful You can only access the dark web with the Tor browser, which prevents. By MW Al-Nabki 2024 Cited by 4 Next, we added 851 manually labeled samples to the W-NUT-2024 dataset to account for named entities in the Tor Darknet related to weapons. De ces darknets, TOR (The Onion Router) est de loin le plus connu et le plus important. Le darwkeb qu'il intgre est trs actif. Defend yourself against tracking and surveillance. Circumvent censorship. Download. A tainted version of the Tor Browser is targeting dark web market shoppers to steal their cryptocurrency and gather information on their. Defend yourself against tracking and surveillance. Circumvent censorship. Anonymity Online.The Tor Project Support Catal (ca. The FBI found Eric Marques by breaking the famed anonymity service Tor, and officials won't reveal if a vulnerability was used. That has.

Buy Bitcoin For Dark Web
With increasingly limited resources, however, spending more in one area needs to be offset by spending less in other areas. According to many news sources like BBC and Independent vaccine passports are now being offered for sale on some popular darknet markets. The dark web is an infamous digital hive of scum and villainy, where people around the world visit their black markets and conduct encrypted business away from any watching eyes. The only reason that the marketplace focuses on cannabis is to distance dark markets andorra itself explicitly from illicit and highly dangerous drugs. Here’s a complete, detailed review of the VPN’s features, as well as a step by step guide on how to use it! So anyone with sufficient funds can place an order without creating an account or depositing funds. Purge Order Data- The market purges the date, which isn’t required anymore. In fact, HiddebWiki is a standard Wikipedia type that has a large amount of information.